Model For The Network Security

A Model For Network Security Pdf A network security model exhibits how the security service has been designed over the network to prevent the opponent from causing a threat to the confidentiality or authenticity of the information that is being transmitted through the network. This model shows that there are four basic tasks in designing a particular security service: design an algorithm for performing the security related transformation. generate the secret information to be used with the algorithm. develop methods for the distribution and sharing of secret information.

Network Security Model Learnbywatch Network security models protect online businesses by using tools like access control, encryption, and antivirus software. examples include zero trust network access (ztna), network access control (nac), and virtual private networks (vpns). Explore the fundamentals of the network security model, its key components, and how it ensures robust protection for your organization. learn best practices with instasafe. Work access security model a general model is illustrated by the above figure 1.6, which reflects a concern for protecting an information. system from unwanted access. most readers are familiar with the concerns caused by the existence of hackers, who attempt to penetrate systems that can. In this article you’ll learn about network security model and its components. a network security model exhibits how the security service has been designed over the network to prevent the opponent from causing a threat to the confidentiality or authenticity of the information that is being transmitted through the network.

Network Security Model Network Security Managed It Services Work access security model a general model is illustrated by the above figure 1.6, which reflects a concern for protecting an information. system from unwanted access. most readers are familiar with the concerns caused by the existence of hackers, who attempt to penetrate systems that can. In this article you’ll learn about network security model and its components. a network security model exhibits how the security service has been designed over the network to prevent the opponent from causing a threat to the confidentiality or authenticity of the information that is being transmitted through the network. Learn about the model for network security, its components, and how it helps in protecting networks from various threats. To understand why network security models are essential, it helps to break down their core components. while specific implementations can vary, most effective models share these fundamental aspects: 1. zero trust architecture. the concept of zero trust is simple: never trust, always verify. This general model shows that there are four basic tasks in designing a particular security service: 1. design an algorithm for performing the security related transformation. the algorithm should be such that an opponent cannot defeat its purpose. 2. generate the secret information to be used with the algorithm. 3. Modeling network security is a powerful approach to identify vulnerabilities and create robust defense strategies. in this post, we’ll explore how to effectively model network security for optimal protection, providing you with practical tools and techniques to safeguard your organization’s valuable data and systems.
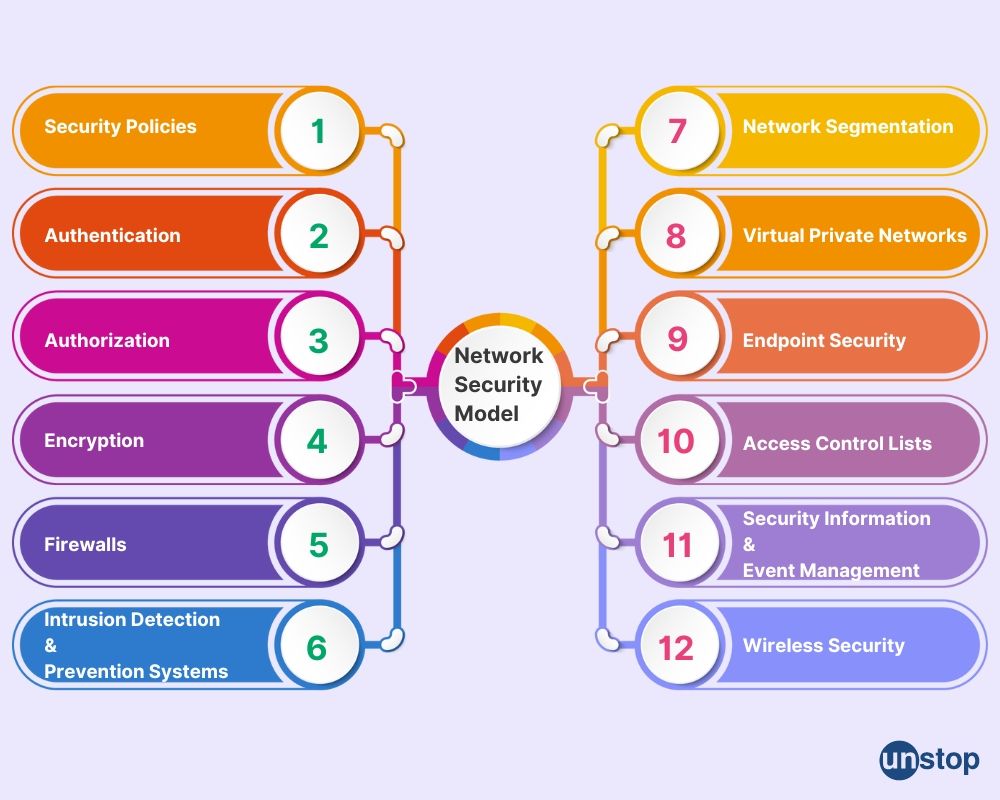
What Is Network Security Model Definition Importance Strategy Unstop Learn about the model for network security, its components, and how it helps in protecting networks from various threats. To understand why network security models are essential, it helps to break down their core components. while specific implementations can vary, most effective models share these fundamental aspects: 1. zero trust architecture. the concept of zero trust is simple: never trust, always verify. This general model shows that there are four basic tasks in designing a particular security service: 1. design an algorithm for performing the security related transformation. the algorithm should be such that an opponent cannot defeat its purpose. 2. generate the secret information to be used with the algorithm. 3. Modeling network security is a powerful approach to identify vulnerabilities and create robust defense strategies. in this post, we’ll explore how to effectively model network security for optimal protection, providing you with practical tools and techniques to safeguard your organization’s valuable data and systems.
What Is Network Security Model Definition Importance Strategy Unstop This general model shows that there are four basic tasks in designing a particular security service: 1. design an algorithm for performing the security related transformation. the algorithm should be such that an opponent cannot defeat its purpose. 2. generate the secret information to be used with the algorithm. 3. Modeling network security is a powerful approach to identify vulnerabilities and create robust defense strategies. in this post, we’ll explore how to effectively model network security for optimal protection, providing you with practical tools and techniques to safeguard your organization’s valuable data and systems.
Comments are closed.